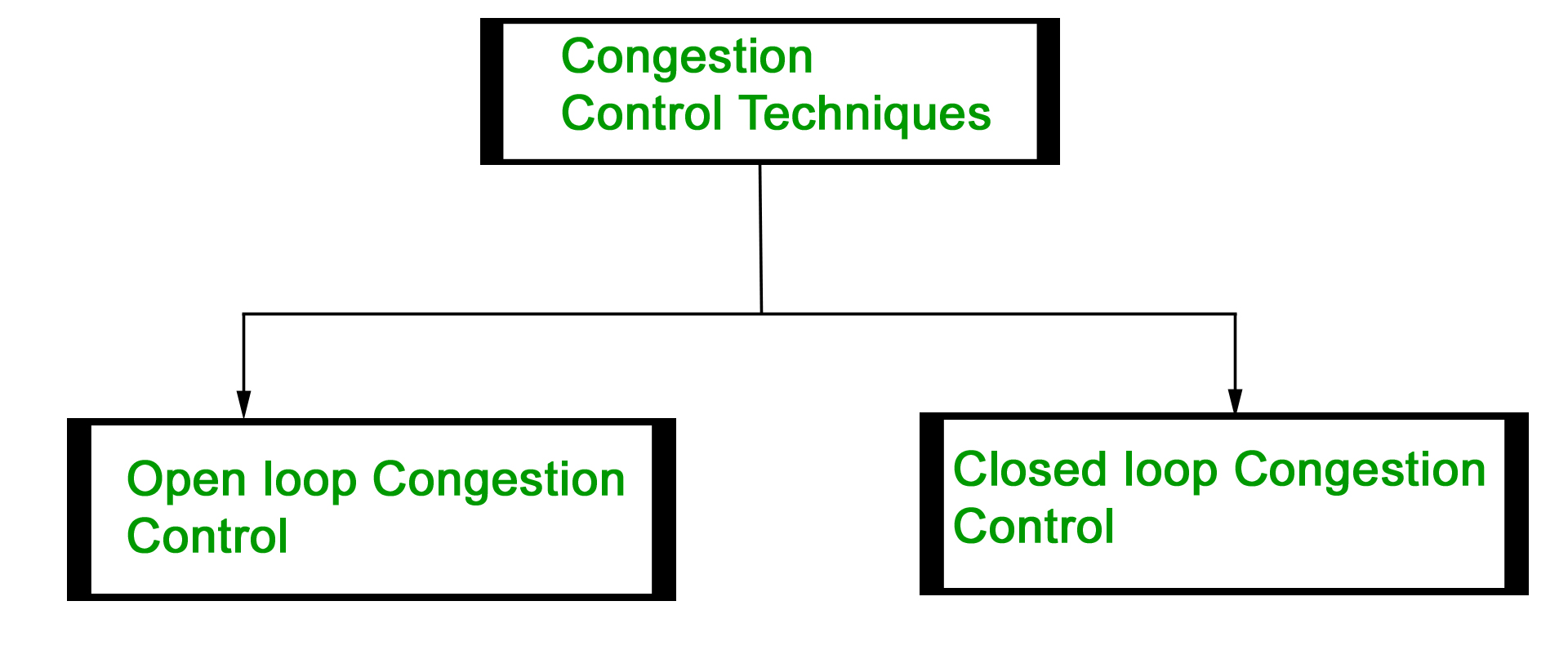
Cryptographic puzzles are a method of protecting against DoS attacks. The idea behind cryptographic puzzles is the following: for a client to connect to a server under attack, he must solve a mathematical puzzle. The difficulty of the puzzle will be directly proportional to the number of connections initiated by the client. Thus, a legitimate client will not notice a big difference when...